...
- Launch Joget from your browser and login as admin.
- Navigate to Settings > License.
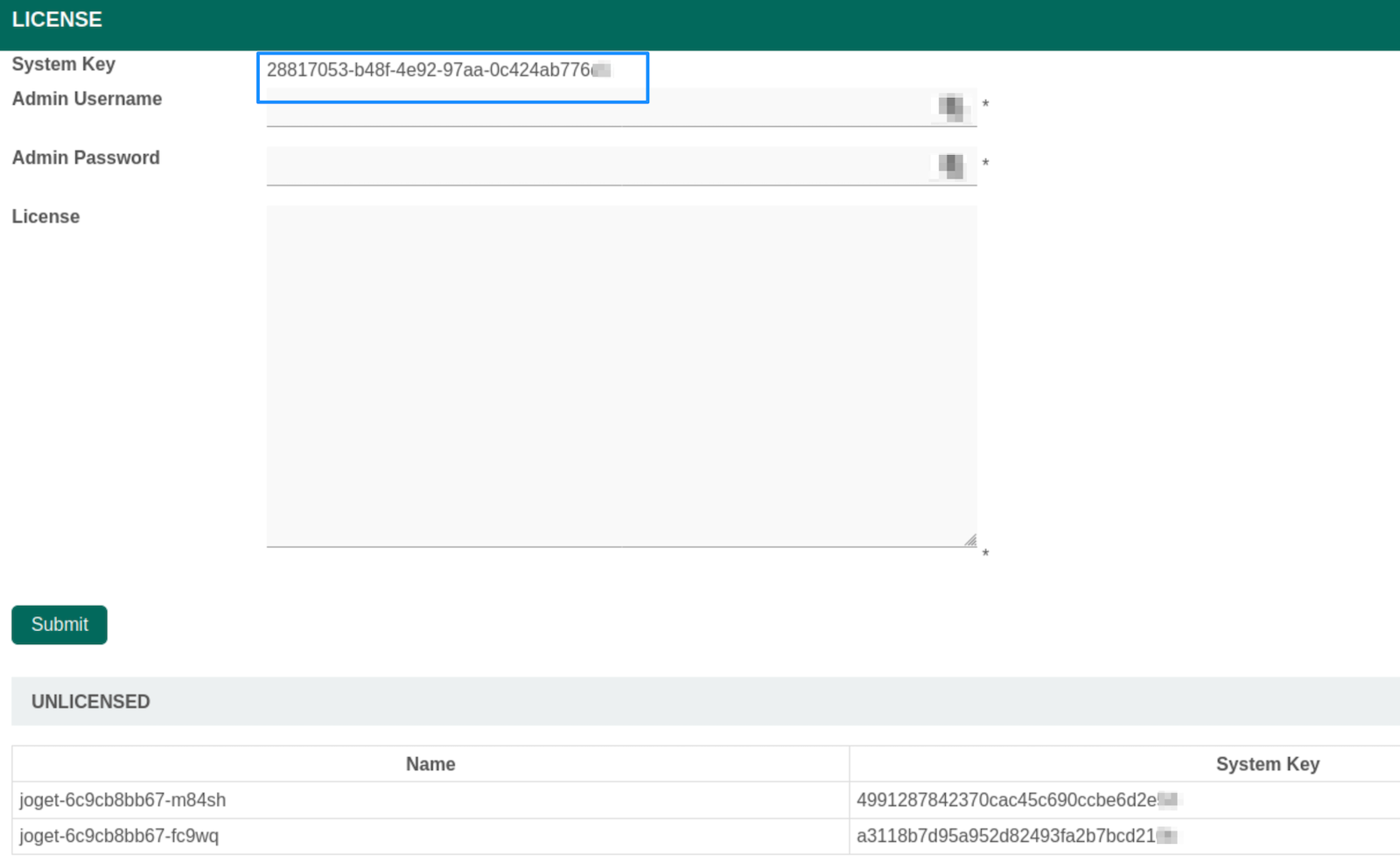
- Your system key should contains dashes as the following.
If the system key matches any of the nodes listed at the bottom, then it is wrong. - If it does not, chances are that you did not assign the service account cluster view permission for Joget to retrieve the deployment info.
Check the logs to look for "io.kubernetes.client.openapi.ApiException: Forbidden".ERROR 14 Apr 2021 12:35:03 org.joget.apps.license.LicenseManager - Forbidden io.kubernetes.client.openapi.ApiException: Forbidden at io.kubernetes.client.openapi.ApiClient.handleResponse(ApiClient.java:971) at io.kubernetes.client.openapi.ApiClient.execute(ApiClient.java:883) at io.kubernetes.client.openapi.apis.CoreV1Api.readNamespacedPodWithHttpInfo(CoreV1Api.java:45995) at io.kubernetes.client.openapi.apis.CoreV1Api.readNamespacedPod(CoreV1Api.java:45965) at org.joget.apps.license.LicenseManager.generateK8sDeploymentSystemKey(LicenseManager.java:934) at org.joget.apps.license.LicenseManager.generateClusterSystemKey(LicenseManager.java:854) at org.joget.apps.license.LicenseManager.checkClusterLicense(LicenseManager.java:1055) at org.joget.apps.license.LicenseManager$4.run(LicenseManager.java:1029)
The "io.kubernetes.client.openapi.ApiException: Forbidden"exception shows this permission is missing. You may need to change namespace value if they are not using the default namespace. Once that you have resolved this error, then only the system key would change back to using the deployment ID.
- The following in the YAML file.
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: joget-dx7-tomcat9-clusterrolebinding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: view
subjects:
- kind: ServiceAccount
name: default
namespace: default
is to assign the service account cluster view permission to retrieve Deployment info for the license system key. - If the RBAC settings of the Kubernetes cluster doesn't allow the use of ClusterRole, you can create a Role and RoleBinding to retrieve the Joget deployment info for the license system key. Use the YAML file below;
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: deployment-info-role
namespace: <namespace-here>
rules:
- apiGroups: ["apps"]
resources: ["replicasets"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: deployment-info-rolebinding
namespace: <namespace-here>
subjects:
- kind: ServiceAccount
name: default
namespace: <namespace-here>
roleRef:
kind: Role
name: deployment-info-role
apiGroup: rbac.authorization.k8s.io