Introduction
OpenID Directory Manager plugin enables the use of OpenID Connect to authenticate users to sign in to Joget.
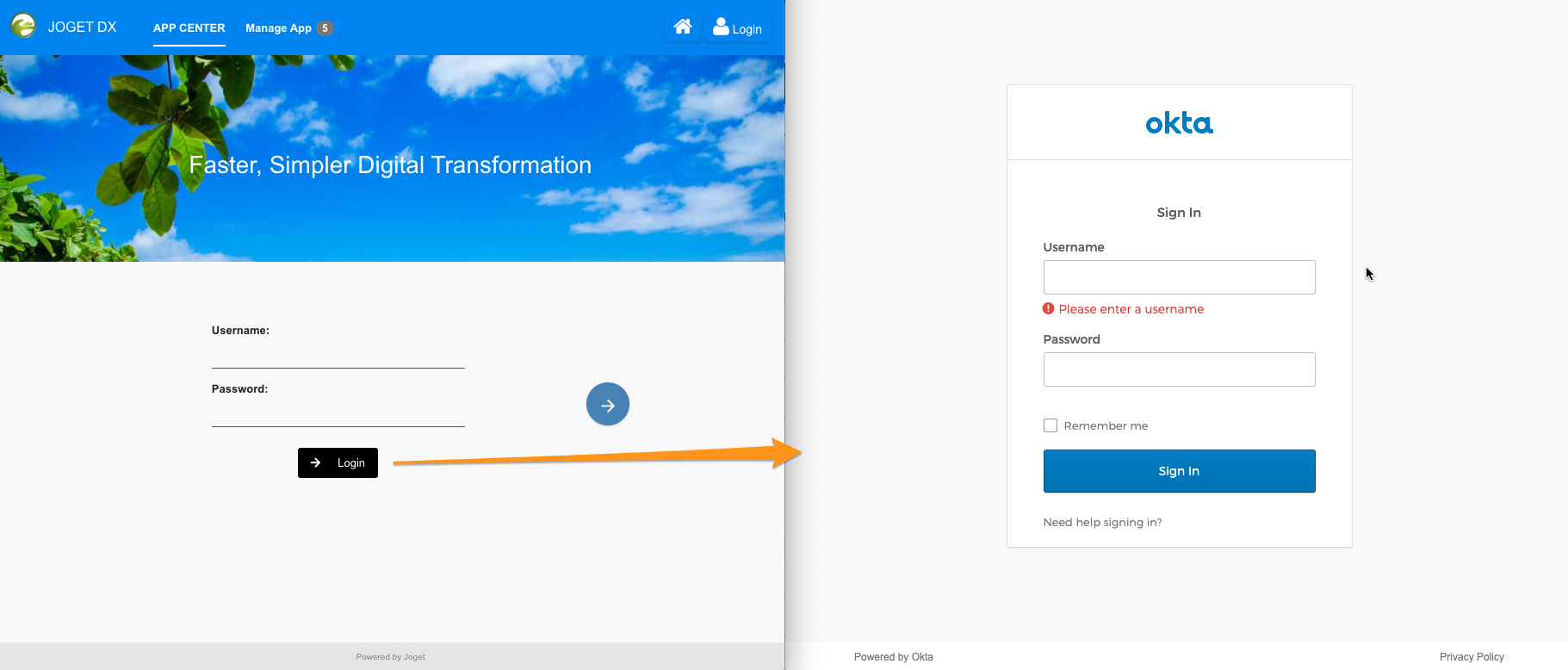
Figure 1: Login screen with an additional sign-in button using OpenID Directory Manager plugin
Upon clicking on the login button, users will be redirected to the configured OpenID Connect site where they will log in. When a user is authenticated, it will then redirect back to Joget using the "Callback URL" configured in the plugin.
This plugin requires the use of Joget Professional edition and above.
This plugin source code is available in a new open source repository at https://github.com/jogetoss/. JogetOSS is a community-led team for open source software related to the Joget no-code/low-code application platform. Projects under JogetOSS are community-driven and community-supported, and you are welcome to contribute to the projects.
Configurations Steps
- Install the OpenID Connect Directory Manager Plugin from the Joget Marketplace.
- In the Joget System Settings > General Settings, set API Domain Whitelist to * (IMPORTANT NOTE: If this is not set, you will get a 400 Forbidden error when performing the SSO)
- In the Joget System Settings > Directory Manager, select the Open ID Connect Plugin.
- Provide the callback URL to your OID provider and obtain the settings to configure in Joget.
- In the OpenID Connect Directory Manager Plugin, configure it according to the settings provided by your OID provider.
OpenID Plugin Configuration
OpenID Provider Details
| Attribute | Description |
|---|---|
| Callback URL | URL to which Auth0 redirects users after they authenticate. Ensure to provide this Callback URL to your OpenID Connect service. |
| Issuer |
|
Issuer URL | URL which is used to validate the discovery URL (Issuer URL + "/.well-known/openid-configuration") URL where Auth0 can find the OpenID Provider Configuration Document, which should be available in the |
| Authorization Token Endpoint | Authorization server's authorization endpoint, which you can retrieve using the server's Metadata URI (Issuer URL + "/.well-known/openid-configuration"). Sample Format https://${Issuer URL}/oauth2/${authServerId}/v1/authorize |
| Token Endpoint | The endpoint on the Authorization Server is used to programmatically request tokens, which you can retrieve using the server's Metadata URI (Issuer URL + "/.well-known/openid-configuration"). Sample Format https://${Issuer URL}/oauth2/${authServerId}/v1/token |
| User Info Endpoint | User Profile Information, which you can retrieve using the server's Metadata URI (Issuer URL + "/.well-known/openid-configuration"). Sample Format https://${Issuer URL}/oauth2/${authServerId}/v1/userinfo |
| Json Web Key Set | Issued by the authorization server and signed using the RS256 signing algorithm Sample Format https://${Issuer URL}/oauth2/${authServerId}/v1/keys |
| Response Types Supported | By default, code |
Client ID | The Client ID provisioned by the OpenID provider when the client was registered |
Client Secret | The Client Secret (password) provisioned by the OpenID provider when the client was registered |
| Scope | A list of Auth0 scopes to request when connecting to the Identify Provider. By default, openid profile email |
User Provisioning Enabled | If enabled, ensures the user account is created in Joget's User Directory |
Configure OpenID Connect Login Button
| Attribute | Description |
|---|---|
Login Button Text | Login button styling text Sample Value Login |
| Login Button Icon | Login button styling icon class Sample Value fas fa-arrow-right |
| Button Text Color | Login button styling button text color Sample Value white |
| Button Background Color | Login button styling button background-color Sample Value black |
Sample Configurations
| Attribute / Provider | OKTA | OKTA | Microsoft Azure AD | Auth0 | |
|---|---|---|---|---|---|
| Issuer | Issuer URL | Custom | Issuer URL | Custom | Issuer URL |
| Issuer URL | https://dev-sample123.okta.com | https://dev-sample123.okta.com | https://accounts.google.com | https://login.microsoftonline.com/tenantIDSampleValue/v2.0 | https://dev-sample123.auth0.com |
| Authorization Token Endpoint | https://dev-sample123.okta.com/oauth2/v1/authorize | https://login.microsoftonline.com/tenantIDSampleValue/oauth2/v2.0/authorize | |||
| Token Endpoint | https://dev-sample123.okta.com/oauth2/v1/token | https://login.microsoftonline.com/tenantIDSampleValue/oauth2/v2.0/token | |||
| User Info Endpoint | https://dev-sample123.okta.com/oauth2/v1userinfo | https://graph.microsoft.com/oidc/userinfo | |||
| Json Web Key Set | https://dev-sample123.okta.com/oauth2/v1/keys | https://login.microsoftonline.com/tenantIDSampleValue /discovery/v2.0/keys | |||
| Responses Types Supported | code | code | code | code | code |
| Client ID | clientIDSampleValue | clientIDSampleValue | clientIDSampleValue | clientIDSampleValue | clientIDSampleValue |
| Client Secret | clientSecretSampleValue | clientSecretSampleValue | clientSecretSampleValue | clientSecretSampleValue | clientSecretSampleValue |
| Scope | openid profile email | openid profile email | openid email | openid profile email | openid profile email |
| Documentation Link | https://developer.okta.com/docs/reference/api/oidc/ | https://developer.okta.com/docs/reference/api/oidc/ | https://developers.google.com/identity/protocols/oauth2/openid-connect | https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-protocols-oidc https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app To obtain all the URL paths, from your Azure App, go to Overview > Endpoints, look for "OpenID Connect metadata document" and open the URL to obtain all the paths. | Connect to OpenID Connect Identity Provider (auth0.com) |
Download Plugin
- For Joget DX Enterprise & Professional editions: Joget Marketplace > View App Details & Download
Change Logs
7.0.3
[ MODIFIED ] : Redirect back to referrer after login.
[ FIXED ] : Fix nonce issue.
7.0.2
[ FIXED ] : Fix Forgot password not displaying on login when enabled.
7.0.1
[ FIXED ] : 404 error on first login by local user after enabling the plugin.
[ FIXED ] : Incorrect SSO URL.
[ MODIFIED ] : Added default values to login button.
7.0.0
[ ADDED ] : Initial Release.